PassLeader released the NEWEST CompTIA SY0-501 exam dumps recently! Both SY0-501 VCE dumps and SY0-501 PDF dumps are available on PassLeader, either SY0-501 VCE dumps or SY0-501 PDF dumps have the NEWEST SY0-501 exam questions in it, they will help you passing CompTIA SY0-501 exam easily! You can download the valid SY0-501 dumps VCE and PDF from PassLeader here: https://www.passleader.com/sy0-501.html (1218 Q&As Dumps –> 1235 Q&As Dumps –> 1292 Q&As Dumps –> 1318 Q&As Dumps –> 1366 Q&As Dumps –> 1423 Q&As Dumps –> 1472 Q&As Dumps) (Wrong Answers Have Been Corrected!!!)
Also, previewing the NEWEST PassLeader SY0-501 dumps online for free on Google Drive: https://drive.google.com/open?id=1Ei1CtZKTLawI_2jpkecHaVbM_kXPMZAu
QUESTION 136
Which of the following attack types BEST describes a client-side attack that is used to mandate an HTML iframe with JavaScript code via web browser?
A. Buffer overflow
B. MITM
C. xss
D. SQLi
Answer: C
QUESTION 137
A company has a data classification system with definitions for “Private” and “Public”. The company’s security policy outlines how data should be protected based on type. The company recently added the data type “Proprietary”. Which of the following is the MOST likely reason the company added this data type?
A. Reduced cost
B. More searchable data
C. Better data classification
D. Expanded authority of the privacy officer
Answer: B
QUESTION 138
A security administrator is developing training for corporate users on basic security principles for personal email accounts. Which of the following should be mentioned as the MOST secure way for password recovery?
A. Utilizing a single Qfor password recovery
B. Sending a PIN to a smartphone through text message
C. Utilizing CAPTCHA to avoid brute force attacks
D. Use a different e-mail address to recover password
Answer: B
QUESTION 139
A company researched the root cause of a recent vulnerability in its software. It was determined that the vulnerability was the result of two updates made in the last release. Each update alone would not have resulted in the vulnerability. In order to prevent similar situations in the future, the company should improve which of the following?
A. Change management procedures.
B. Job rotation policies.
C. Incident response management.
D. Least privilege access controls.
Answer: A
QUESTION 140
A computer on a company network was infected with a zero-day exploit after an employee accidently opened an email that contained malicious content. The employee recognized the email as malicious and was attempting to delete it, but accidently opened it. Which of the following should be done to prevent this scenario from occurring again in the future?
A. Install host-based firewalls on all computers that have an email client installed.
B. Set the email program default to open messages in plain text.
C. Install end-point protection on all computers that access web email.
D. Create new email spam filters to delete all messages from that sender.
Answer: C
QUESTION 141
A company wants to ensure that the validity of publicly trusted certificates used by its web server can be determined even during an extended internet outage. Which of the following should be implemented?
A. Recovery agent
B. Ocsp
C. Crl
D. Key escrow
Answer: B
QUESTION 142
An administrator intends to configure an IPSec solution that provides ESP with integrity protection, but not confidentiality protection. Which of the following AES modes of operation would meet this integrity-only requirement?
A. HMAC
B. PCBC
C. CBC
D. GCM
E. CFB
Answer: A
QUESTION 143
The Chief Security Officer (CSO) has issued a new policy that requires that all internal websites be configured for HTTPS traffic only. The network administrator has been tasked to update all internal sites without incurring additional costs. Which of the following is the best solution for the network administrator to secure each internal website?
A. Use certificates signed by the company CA.
B. Use a signing certificate as a wild card certificate.
C. Use certificates signed by a public CA.
D. Use a self-signed certificate on each internal server.
Answer: D
QUESTION 144
A security program manager wants to actively test the security posture of a system. The system is not yet in production and has no uptime requirement or active user base. Which of the following methods will produce a report which shows vulnerabilities that were actually exploited?
A. Peer review
B. Component testing
C. Penetration testing
D. Vulnerability testing
Answer: C
Explanation:
A penetration test, or pen test, is an attempt to evaluate the security of an IT infrastructure by safely trying to exploit vulnerabilities.
QUESTION 145
A new intern in the purchasing department requires read access to shared documents. Permissions are normally controlled through a group called “purchasing”, however, the purchasing group permissions allow write access. Which of the following would be the BEST course of action?
A. Modify all the shared files with read only permissions for the intern.
B. Create a new group that has only read permissions for the files.
C. Remove all permissions for the shared files.
D. Add the intern to the “purchasing” group.
Answer: B
QUESTION 146
A business has recently deployed laptops to all sales employees. The laptops will be used primarily from home offices and while traveling, and a high amount of wireless mobile use is expected. To protect the laptops while connected to untrusted wireless networks, which of the following would be the BEST method for reducing the risk of having the laptops compromised?
A. MAC filtering
B. Virtualization
C. OS hardening
D. Application white-listing
Answer: C
QUESTION 147
A security engineer is configuring a system that requires the X.509 certificate information to be pasted into a form field in Base64 encoded format to import it into the system. Which of the following certificate formats should the engineer use to obtain the information in the required format?
A. PFX
B. PEM
C. DER
D. CER
Answer: B
QUESTION 148
When performing data acquisition on a workstation, which of the following should be captured based on memory volatility? (Select TWO.)
A. USB-attached hard disk
B. Swap/pagefile
C. Mounted network storage
D. ROM
E. RAM
Answer: AD
QUESTION 149
When configuring settings in a mandatory access control environment, which of the following specifies the subjects that can access specific data objects?
A. Owner
B. System
C. Administrator
D. User
Answer: C
QUESTION 150
A systems administrator is reviewing the following information from a compromised server:
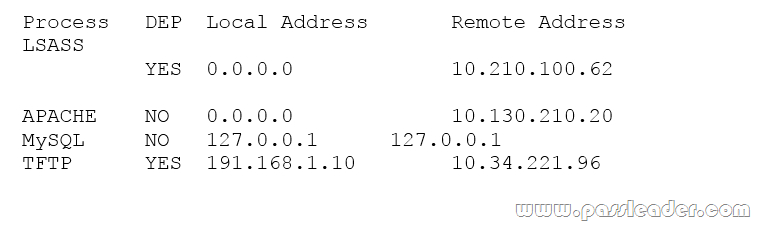
Given the above information, which of the following processes was MOST likely exploited via a remote buffer overflow attack?
A. APACHE
B. LSASS
C. MySQL
D. TFTP
Answer: A
Welcome to choose PassLeader SY0-501 dumps for 100% passing CompTIA SY0-501 exam: https://www.passleader.com/sy0-501.html (1218 Q&As VCE Dumps and PDF Dumps –> 1235 Q&As VCE Dumps and PDF Dumps –> 1292 Q&As VCE Dumps and PDF Dumps –> 1318 Q&As VCE Dumps and PDF Dumps –> 1366 Q&As VCE Dumps and PDF Dumps –> 1423 Q&As VCE Dumps and PDF Dumps –> 1472 Q&As VCE Dumps and PDF Dumps) (Wrong Answers Have Been Corrected!!!)
Also, previewing the NEWEST PassLeader SY0-501 dumps online for free on Google Drive: https://drive.google.com/open?id=1Ei1CtZKTLawI_2jpkecHaVbM_kXPMZAu