PassLeader released the NEWEST CompTIA CAS-003 exam dumps recently! Both CAS-003 VCE dumps and CAS-003 PDF dumps are available on PassLeader, either CAS-003 VCE dumps or CAS-003 PDF dumps have the NEWEST CAS-003 exam questions in it, they will help you passing CompTIA CAS-003 exam easily! You can download the valid CAS-003 dumps VCE and PDF from PassLeader here: https://www.passleader.com/cas-003.html (726 Q&As Dumps –> 763 Q&As Dumps –> 827 Q&As Dumps –> 863 Q&As Dumps –> 894 Q&As Dumps –> 974 Q&As Dumps)
Also, previewing the NEWEST PassLeader CAS-003 dumps online for free on Google Drive: https://drive.google.com/open?id=1bfoVeMAPqLPPEtiIibD38-i-xMle-2O0
NEW QUESTION 700
A company is implementing a new secure identity application, given the following requirements:
– The cryptographic secrets used in the application must never be exposed to users or the OS.
– The application must work on mobile devices.
– The application must work with the company’s badge reader system.
Which of the following mobile device specifications are required for this design? (Choose two.)
A. Secure element
B. Biometrics
C. UEFI
D. SEAndroid
E. NFC
F. HSM
Answer: BE
NEW QUESTION 701
Which of the following risks does expanding business into a foreign country carry?
A. Data sovereignty laws could result in unexpected liability.
B. Export controls might decrease software costs.
C. Data ownership might revert to the regulatory entities in the new country.
D. Some security tools might be monitored by legal authorities.
Answer: A
NEW QUESTION 702
A red team is able to connect a laptop with penetration testing tools directly into an open network port. The team then is able to take advantage of a vulnerability on the domain controller to create and promote a new enterprise administrator. Which of the following technologies would MOST likely eliminate this attack vector m the future?
A. Monitor for anomalous creations of privileged domain accounts.
B. Install a NIPS with rules appropriate to drop most exploit traffic.
C. Ensure the domain controller has the latest security patches.
D. Implement 802.1X with certificate-based authentication.
Answer: C
NEW QUESTION 703
A secure facility has a server room that currently is controlled by a simple lock and key. and several administrators have copies of the key. To maintain regulatory compliance, a second lock, which is controlled by an application on the administrators’ smartphones, is purchased and installed. The application has various authentication methods that can be used. The criteria for choosing the most appropriate method are:
– It cannot be invasive to the end user.
– It must be utilized as a second factor.
– Information sharing must be avoided.
– It must have a low false acceptance rate.
Which of the following BEST meets the criteria?
A. Facial recognition
B. Swipe pattern
C. Token card
D. Complex passcode
E. Fingerprint scanning
Answer: E
NEW QUESTION 704
A company is purchasing an application that will be used to manage all IT assets as well as provide an incident and problem management solution for IT activity. The company narrows the search to two products. Application A and Application B; which meet all of its requirements. Application A is the most cost-effective product, but it is also the riskiest so the company purchases Application B. Which of the following types of strategies did the company use when determining risk appetite?
A. Mitigation
B. Acceptance
C. Avoidance
D. Transfer
Answer: B
NEW QUESTION 705
A company is the victim of a phishing and spear-phishing campaign. Users are Clicking on website links that look like common bank sites and entering their credentials accidentally. A security engineer decides to use a layered defense to prevent the phishing or lessen its impact. Which of the following should the security engineer implement? (Choose two.)
A. Spam filter
B. Host intrusion prevention
C. Client certificates
D. Content filter
E. Log monitoring
F. Data loss prevention
Answer: AE
NEW QUESTION 706
An enterprise solution requires a central monitoring platform to address the growing networks of various departments and agencies that connect to the network. The current vendor products are not adequate due to the growing number of heterogeneous devices. Which of the following is the primary concern?
A. Scalability
B. Usability
C. Accountability
D. Performance
Answer: A
NEW QUESTION 707
As part of a systems modernization program, the use of a weak encryption algorithm is identified m a wet se-vices API. The client using the API is unable to upgrade the system on its end which would support the use of a secure algorithm set. As a temporary workaround the client provides its IP space and the network administrator Limits access to the API via an ACL to only the IP space held by the client. Which of the following is the use of the ACL in this situation an example of?
A. Avoidance
B. Transference
C. Acceptance
D. Mitigation
E. Assessment
Answer: D
NEW QUESTION 708
The Chief Financial Officer (CFO) of a major hospital system has received a ransom letter that demands a large sum of cryptocurrency be transferred to an anonymous account. If the transfer does not take place within ten hours, the letter states that patient information will be released on the dark web. A partial listing of recent patients is included in the letter. This is the first indication that a breach took place. Which of the following steps should be done FIRST?
A. Review audit logs to determine the extent of the breach.
B. Pay the hacker under the condition that all information is destroyed.
C. Engage a counter-hacking team to retrieve the data.
D. Notify the appropriate legal authorities and legal counsel.
Answer: D
NEW QUESTION 709
To meet a SLA, which of the following documents should be drafted, defining the company’s internal interdependent unit responsibilities and delivery timelines?
A. BPA
B. OLA
C. MSA
D. MOU
Answer: B
NEW QUESTION 710
The security administrator of a small firm wants to stay current on the latest security vulnerabilities and attack vectors being used by crime syndicates and nation-states. The information must be actionable and reliable. Which of the following would BEST meet the needs of the security administrator?
A. Software vendor threat reports
B. White papers
C. Security blogs
D. Threat data subscription
Answer: D
NEW QUESTION 711
An organization is moving internal core data-processing functions related to customer data to a global public cloud provider that uses aggregated services from other partner organizations. Which of the following compliance issues will MOST likely be introduced as a result of the migration?
A. Internal data integrity standards and outsourcing contracts and partnerships.
B. Data ownership, internal data classification, and risk profiling of outsourcers.
C. Company audit functions, cross-boarding jurisdictional challenges, and export controls.
D. Data privacy regulations, data sovereignty, and third-party providers.
Answer: D
NEW QUESTION 712
A security administrator is investigating an incident involving suspicious word processing documents on an employee’s computer, which was found powered off in the employee’s office. Which of the following tools is BEST suited for extracting full or partial word processing documents from unallocated disk space?
A. memdump
B. forenoat
C. dd
D. nc
Answer: B
NEW QUESTION 713
The email administrator must reduce the number of phishing emails by utilizing more appropriate security controls. The following configurations already are in place:
– Keyword Mocking based on word lists.
– URL rewriting and protection.
– Stopping executable files from messages.
Which of the following is the BEST configuration change for the administrator to make?
A. Configure more robust word lists for blocking suspicious emails.
B. Configure Bayesian filtering to block suspicious inbound email.
C. Configure appropriate regular expression rules per suspicious email received.
D. Configure the mail gateway to strip any attachments.
Answer: C
NEW QUESTION 714
Within the past six months, a company has experienced a series of attacks directed at various collaboration tools. Additionally, sensitive information was compromised during a recent security breach of a remote access session from an unsecure site. As a result, the company is requiring all collaboration tools to comply with the following:
– Secure messaging between internal users using digital signatures.
– Secure sites for video-conferencing sessions.
– Presence information for all office employees.
– Restriction of certain types of messages to be allowed into the network.
Which of the following applications must be configured to meet the new requirements? (Choose two.)
A. Remote desktop
B. VoIP
C. Remote assistance
D. Email
E. Instant messaging
F. Social media websites
Answer: BE
NEW QUESTION 715
A government entity is developing requirements for an RFP to acquire a biometric authentication system. When developing these requirements, which of the following considerations is MOST critical to the verification and validation of the SRTM?
A. Local and national laws and regulations.
B. Secure software development requirements.
C. Environmental constraint requirements.
D. Testability of requirements.
Answer: A
NEW QUESTION 716
A SaaS provider decides to offer data storage as a service. For simplicity, the company wants to make the service available over industry standard APIs, routable over the public Internet. Which of the following controls offers the MOST protection to the company and its customers’ information?
A. Detailed application logging.
B. Use of non-standard ports.
C. Web application firewall.
D. Multifactor authentication.
Answer: D
NEW QUESTION 717
A security administrator wants to stand up a NIPS that is multilayered and can incorporate many security technologies into a single platform. The product should have diverse capabilities, such as antivirus, VPN, and firewall services, and be able to be updated in a timely manner to meet evolving threats. Which of the following network prevention system types can be used to satisfy the requirements?
A. Application firewall
B. Unified threat management
C. Enterprise firewall
D. Content-based IPS
Answer: A
NEW QUESTION 718
The Chief Financial Officer (CFO) of an organization wants the IT department to add the CFO’s account to the domain administrator group. The IT department thinks this is nsky and wants support from the security manager before proceeding. Which of the following BEST supports the argument against providing the CFO with domain administrator access?
A. Discretionary access control.
B. Separation of duties.
C. Data classification.
D. Mandatory access control.
Answer: B
NEW QUESTION 719
A manufacturing company employs SCADA systems to drive assembly lines across geographically dispersed sites. Therefore, the company must use the Internet to transport control messages and responses. Which of the following architectural changes when integrated will BEST reduce the manufacturing control system’s attack surface? (Choose two.)
A. Design a patch management capability for control systems.
B. Implement supply chain security.
C. Integrate message authentication.
D. Add sensors and collectors at the Internet boundary.
E. Isolate control systems from enterprise systems.
F. Implement a site-to-site VPN across sites.
Answer: AE
NEW QUESTION 720
The Chief Information Security Officer (CISO) is preparing a requirements matrix scorecard for a new security tool the company plans to purchase. Feedback from which of the following documents will provide input for the requirements matrix scorecard during the vendor selection process?
A. MSA
B. RFQ
C. RFI
D. RFP
Answer: D
NEW QUESTION 721
An information security officer reviews a report and notices a steady increase in outbound network traffic over the past ten months. There is no clear explanation for the increase. The security officer interviews several business units and discovers an unsanctioned cloud storage provider was used to share marketing materials with potential customers. Which of the following services would be BEST for the security officer to recommend to the company?
A. NIDS
B. HIPS
C. CASB
D. SFTP
Answer: C
NEW QUESTION 722
A researcher is working to identify what appears to be a new variant of an existing piece of malware commonly used in ransomware attacks. While it is not identical to the malware previously evaluated. it has a number of similarities including language, payload. and algorithms. Which of the following would help the researcher safely compare the code base of the two variants?
A. Virtualized sandbox
B. Vulnerability scanner
C. Software-defined network
D. HTTP interceptor
Answer: A
NEW QUESTION 723
After the departure of a developer under unpleasant circumstances, the company is concerned about the security of the software to which the developer has access. Which of the following is the BEST way to ensure security of the code following the incident?
A. Hire an external red tem to conduct black box testing.
B. Conduct a peer review and cross reference the SRTM.
C. Perform white-box testing on all impacted finished products.
D. Perform regression testing and search for suspicious code.
Answer: D
NEW QUESTION 724
A legal services company wants to ensure emails to clients maintain integrity in transit. Which of the following would BEST meet this requirement? (Choose two.)
A. Signing emails to clients with the organization’s public key.
B. Using the organization’s private key to encrypt all communication.
C. Implementing a public key infrastructure.
D. Signing emails to clients with the organization’s private key.
E. Using shared secret keys.
F. Hashing all outgoing emails.
Answer: DF
NEW QUESTION 725
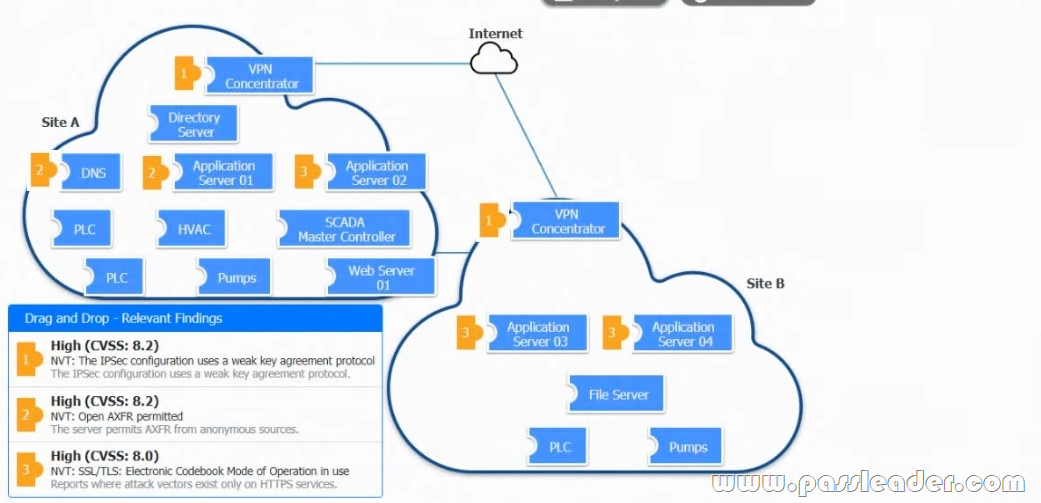
Drag and Drop
A vulnerability scan with the latest definitions was performed across Sites A and B. Match each relevant finding to the affected host-After associating the finding with the appropriate host(s), click the host to select the appropriate corrective action for that finding.
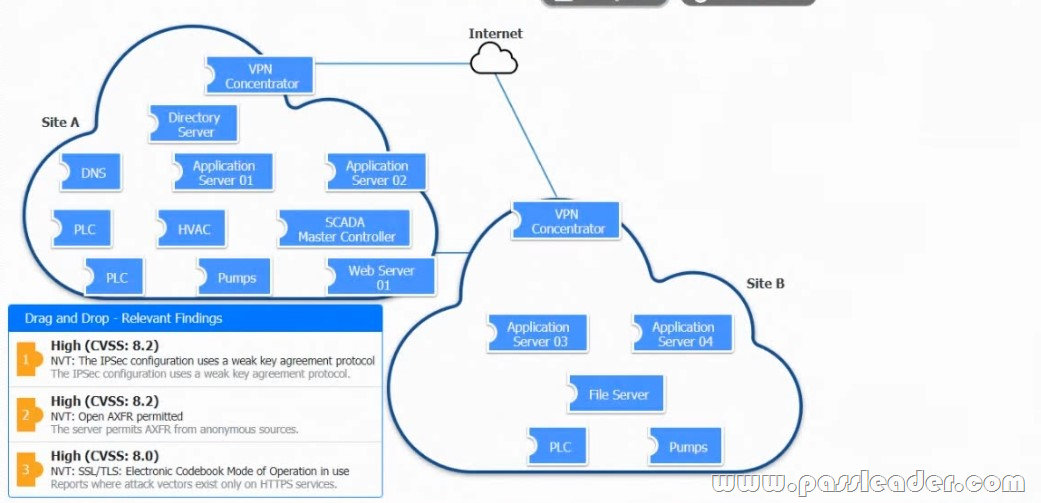
NEW QUESTION 726
……
Welcome to choose PassLeader CAS-003 dumps for 100% passing CompTIA CAS-003 exam: https://www.passleader.com/cas-003.html (726 Q&As VCE Dumps and PDF Dumps –> 763 Q&As VCE Dumps and PDF Dumps –> 827 Q&As VCE Dumps and PDF Dumps –> 863 Q&As VCE Dumps and PDF Dumps –> 894 Q&As VCE Dumps and PDF Dumps –> 974 Q&As VCE Dumps and PDF Dumps)
Also, previewing the NEWEST PassLeader CAS-003 dumps online for free on Google Drive: https://drive.google.com/open?id=1bfoVeMAPqLPPEtiIibD38-i-xMle-2O0