PassLeader released the NEWEST CompTIA CAS-002 exam dumps recently! Both CAS-002 VCE dumps and CAS-002 PDF dumps are available on PassLeader, either CAS-002 VCE dumps or CAS-002 PDF dumps have the NEWEST CAS-002 exam questions in it, they will help you passing CompTIA CAS-002 exam easily! You can download the valid CAS-002 dumps VCE and PDF from PassLeader here: https://www.passleader.com/cas-002.html (900 Q&As Dumps)
Also, previewing the NEWEST PassLeader CAS-002 dumps online for free on Google Drive: https://drive.google.com/open?id=0B-ob6L_QjGLpenQtV3dLMDkyM0U
QUESTION 646
How many levels of threats are faced by the SAN?
A. 3
B. 7
C. 2
D. 5
Answer: A
Explanation:
Storage area network transfers and stores crucial data; often, this makes storage area network vulnerable to risks. There are three different levels of threats faced by the SAN:
– Level one: These types of threats are unintentional and may result in downtime and loss of revenue. However, administrators can prevent these threats.
– Level two: These types of threats are simple malicious attacks that use existing equipments.
– Level three: These types of threats are large scale attacks and are difficult to prevent. These threats come from skilled attackers using uncommon equipments.
QUESTION 647
Which of the following is a written document and is used in those cases where parties do not imply a legal commitment or in those situations where the parties are unable to create a legally enforceable agreement?
A. Patent law
B. Memorandum of understanding (MOU)
C. Memorandum of agreement (MOA)
D. Certification and Accreditation (COA or CnA)
Answer: B
Explanation:
A memorandum of understanding (MOU) is a document that defines a bilateral or multilateral agreement between two parties. This document specifies a convergence of will between the parties, representing a proposed common line of action. A memorandum of understanding (MOU) is generally used in those cases where parties do not imply a legal commitment or in those situations where the parties are unable to create a legally enforceable agreement. It is a proper substitute of a gentlemen’s agreement.
Incorrect:
Not A: Patent laws are used to protect the duplication of software. Software patents cover the algorithms and techniques that are used in creating the software. It does not cover the entire program of the software. Patents give the author the right to make and sell his product. The time of the patent of a product is limited though, i.e., the author of the product has the right to use the patent for only a specific length of time.
Not C: A memorandum of agreement (MOA) is a document that is written between two parties to cooperatively work together on a project for meeting the pre-decided objectives. The principle of an MOA is to keep a written understanding of the agreement between two parties.
QUESTION 648
Which of the following statements are true about capability-based security?
A. It is a concept in the design of secure computing systems, one of the existing security models.
B. It is a computer security model based on the Actor model of computation.
C. It is a scheme used by some computers to control access to memory.
D. It is a concept in the design of secure computing systems.
Answer: D
Explanation:
Capability-based security is a concept in the design of secure computing systems. A capability (known in some systems as a key) is a communicable, unforgivable token of authority. It refers to a value that references an object along with an associated set of access rights. A user program on a capability-based operating system must use a capability to access an object. Capability-based security refers to the principle of designing user programs such that they directly share capabilities with each other according to the principle of least privilege, and to the operating system infrastructure necessary to make such transactions efficient and secure. Although most operating systems implement a facility which resembles capabilities, they typically do not provide enough support to allow for the exchange of capabilities among possibly mutually untrusting entities to be the primary means of granting and distributing access rights throughout the system. A capability-based system, in contrast, is designed with that goal in mind. Answer options B, C, and A are incorrect. These are not correct statements about capability based security.
QUESTION 649
A helpdesk manager at a financial company has received multiple reports from employees and customers that their phone calls sound metallic on the voice system. The helpdesk has been using VoIP lines encrypted from the handset to the PBX for several years. Which of the following should be done to address this issue for the future?
A. SIP session tagging and QoS
B. A dedicated VLAN
C. Lower encryption setting
D. Traffic shaping
Answer: B
QUESTION 650
Lab Simulation
The IDS has detected abnormal behavior on this network. Based on the following screenshots, the following tasks need to be completed:
* Select the server that is a victim of a SQL injection attack.
* Select the source of the buffer overflow attack.
* Modify the access control list (ACL) on the router(s) to ONLY block the buffer overflow attack.
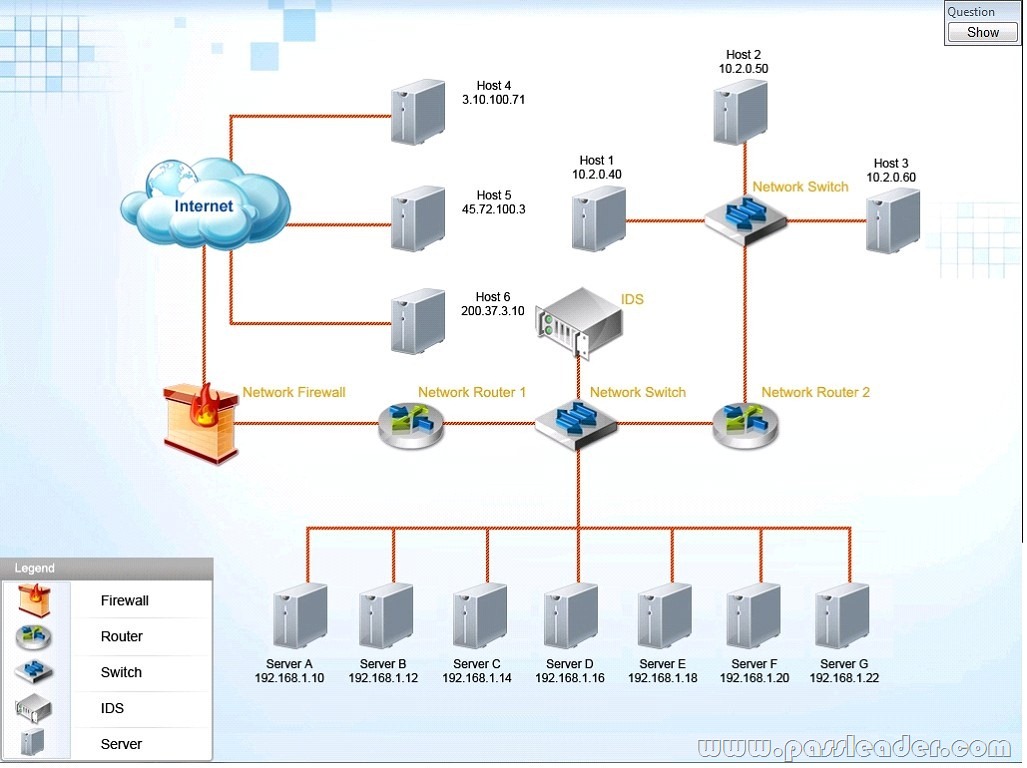


Answer:
First, we need to determine the source of the attack and the victim. View the IDS logs to determine this information. Although SIMs may vary, one example clearly shows the source of the attack as the 10.2.0.50 host, and the victim is Server D. To block only this traffic we need to modify the following rule on router 2 only:
* Source address = 10.2.0.50
* Destination address = 192.168.1.0/24
Deny box should be checked.
Welcome to choose PassLeader CAS-002 dumps for 100% passing CompTIA CAS-002 exam: https://www.passleader.com/cas-002.html (900 Q&As VCE Dumps and PDF Dumps)
Also, previewing the NEWEST PassLeader CAS-002 dumps online for free on Google Drive: https://drive.google.com/open?id=0B-ob6L_QjGLpenQtV3dLMDkyM0U